ARP poisoning, DNS spoofing, and MAC flooding
1. ARP Poisoning (ARP Spoofing)
- ARP (Address Resolution Protocol) maps IP addresses to MAC addresses.
- ARP poisoning involves sending fake ARP messages to a local network, linking the attacker's MAC address to the IP address of another device (e.g., a gateway or server).
Example:
- Scenario: An attacker sends spoofed ARP responses to the network, associating their MAC address with the router's IP address. All traffic intended for the router is now sent to the attacker, enabling Man-in-the-Middle (MITM) attacks.
Impact:
- Data interception.
- Session hijacking.
- Traffic redirection.
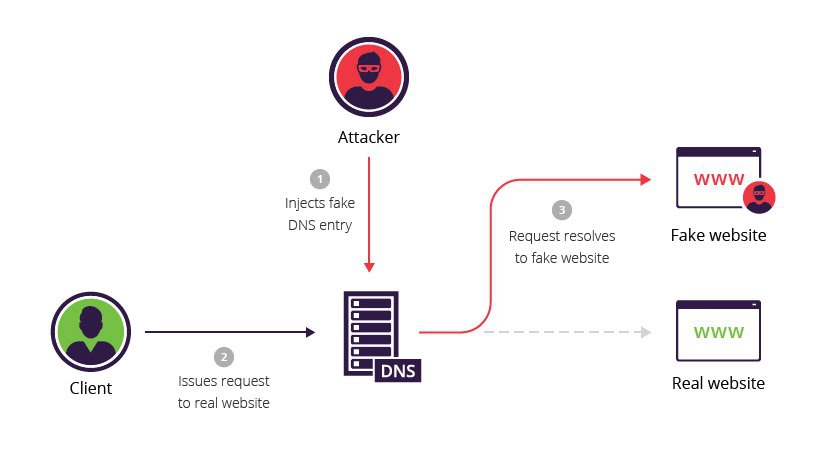
2. DNS Spoofing (DNS Cache Poisoning)
- DNS resolves domain names (e.g., example.com) to IP addresses.
- DNS spoofing involves injecting malicious DNS records into a DNS server or cache, redirecting users to fraudulent websites.
Working
DNS spoofing exploits vulnerabilities in the DNS and its associated protocols. An attacker can carry out this attack in several ways:
- Using Address Resolution Protocol (ARP) to intercept router traffic and manipulate domain name resolution records.
- Altering the records of an authoritative DNS server to redirect users to a fraudulent website.
- Targeting an intermediate name server and exploiting weaknesses in its caching system to execute a Man-in-the-Middle (MITM) attack.
Example:
- Scenario: A user types bank.com, expecting to visit their bank's website. However, a compromised DNS server resolves bank.com to an attacker's phishing site, where credentials are stolen.
Impact:
- Phishing attacks.
- Malware distribution.
- Data theft.
3. MAC Flooding
- MAC flooding involves overwhelming a switch's MAC address table with a flood of spoofed MAC addresses.
- When the table is full, the switch fails open and starts broadcasting traffic to all ports, exposing network data.
Example:
- Scenario: An attacker floods the switch with packets containing fake MAC addresses. The switch's memory overflows, causing it to act like a hub, allowing the attacker to sniff all network traffic.
Impact:
- Loss of confidentiality (data exposure).
- Denial of Service (DoS) on the switch.