Vulnerability scanning and patch management
Vulnerability Scanning and Patch Management
Vulnerability scanning and patch management are critical components of an organization's cybersecurity strategy. Together, they help identify, assess, and remediate vulnerabilities in systems, networks, and software to prevent security breaches.
1. Vulnerability Scanning
Definition:
Vulnerability scanning is the automated process of identifying security weaknesses in systems, networks, and software. It helps uncover known vulnerabilities, misconfigurations, and outdated software that could be exploited.
How Vulnerability Scanning Works:
- Asset Discovery:
- Identifies devices, services, and software in the network (e.g., servers, routers, endpoints).
- Vulnerability Identification:
- Compares the identified assets against a database of known vulnerabilities, such as the Common Vulnerabilities and Exposures (CVE) list.
- Scanning Techniques:
- Credentialed Scanning: Uses admin credentials for in-depth analysis.
- Non-Credentialed Scanning: Simulates an external attack without privileged access.
- Severity Rating:
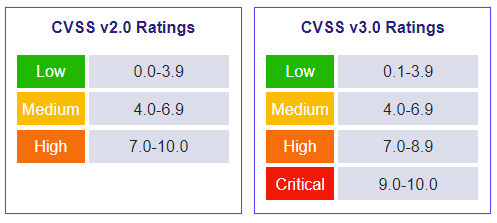
- Vulnerabilities are often ranked using the CVSS (Common Vulnerability Scoring System), which assigns scores (0-10) based on severity.
- Reporting:
- Generates detailed reports on identified vulnerabilities, risk levels, and remediation suggestions.
Common Tools for Vulnerability Scanning:
- Nessus (Tenable): Comprehensive tool for vulnerability scanning.
- OpenVAS: Open-source scanner for vulnerability detection.
- QualysGuard: Cloud-based vulnerability management platform.
- Nmap: Network mapper with basic vulnerability scanning capabilities.
- Rapid7 Nexpose: Scans networks and systems for security weaknesses.
Benefits of Vulnerability Scanning:
- Identifies security weaknesses before attackers can exploit them.
- Provides a clear inventory of outdated or unpatched systems.
- Supports compliance with standards like PCI DSS, HIPAA, and ISO 27001.
- Prioritizes vulnerabilities based on risk severity.
2. Patch Management
Definition:
Patch management is the process of acquiring, testing, deploying, and verifying software updates (patches) to fix vulnerabilities, improve performance, or add features.
Steps in Patch Management:
- Asset Identification:
- Identify all devices, operating systems, and software requiring updates.
- Patch Monitoring:
- Continuously monitor vendor websites, mailing lists, and vulnerability databases for new patches.
- Patch Testing:
- Test patches in a non-production environment to ensure compatibility and stability.
- Patch Deployment:
- Deploy patches in a phased manner (e.g., critical systems first).
- Verification:
- Confirm that the patches are successfully applied and systems are secure.
- Documentation:
- Maintain records of applied patches, affected systems, and compliance reports.
Tools for Patch Management:
- WSUS (Windows Server Update Services): For Windows systems.
- Microsoft SCCM: Manages updates and deployments across enterprise systems.
- SolarWinds Patch Manager: Automates patching for Windows and third-party applications.
- ManageEngine Patch Manager Plus: Cross-platform patch management tool.
- IBM BigFix: Automates patch deployment across large networks.
Patch Management Best Practices:
- Prioritize Critical Patches:
- Use vulnerability ratings (e.g., CVSS) to prioritize patches for high-severity vulnerabilities.
- Automate Patch Deployment:
- Use automated tools to schedule and deploy patches efficiently.
- Test Before Deployment:
- Test patches in a controlled environment to avoid breaking systems.
- Monitor Patch Status:
- Regularly monitor systems to ensure all patches are applied successfully.
- Maintain a Patch Policy:
- Establish clear policies for patch cycles, updates, and emergency patches.
- Backup Systems Before Patching:
- Ensure data recovery options are available in case of patch failures.

ref: watchgourd.com
Key Differences: Vulnerability Scanning vs. Patch Management
|
Aspect |
Vulnerability Scanning |
Patch Management |
|
Objective |
Identify vulnerabilities in systems. |
Remediate vulnerabilities by applying patches. |
|
Tools |
Nessus, OpenVAS, QualysGuard. |
WSUS, SCCM, SolarWinds. |
|
Process |
Scanning for weaknesses and reporting. |
Testing, deploying, and verifying patches. |
|
Output |
Vulnerability report with severity ratings. |
Updated and secured systems. |
|
Frequency |
Regularly (e.g., weekly, monthly scans). |
Periodic or based on critical updates. |
Challenges in Vulnerability Scanning and Patch Management:
- Resource Constraints:
- Scanning and patching require time and skilled personnel.
- Patch Compatibility:
- Patches may conflict with legacy systems or software.
- Prioritization:
- Sorting through large numbers of vulnerabilities and updates can be overwhelming.
- Downtime:
- Patching systems may cause temporary outages, disrupting operations.
- Unpatched Endpoints:
- Remote or off-network systems may not receive patches.